|
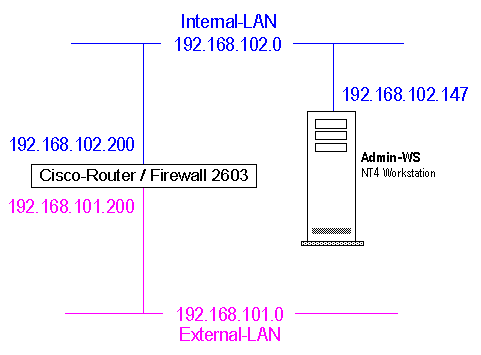
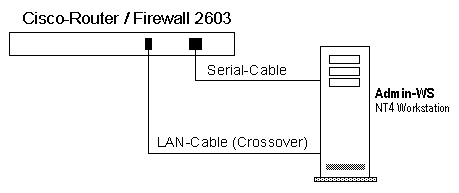
Connect the NT4 Admin-Workstation on COM1 or COM2 using the blue RS-232
cable delivered with the CONSOLE-Port on the CISCO Router. This connection is used as the
Router Console, to enter commands and to verify the boot process. To down- and upload the
IOS image and configuration file a crossover LAN cable is needed. After booting the router,
you will see the following messages in TeraTermPro (Terminal Emulation Software).
System Bootstrap, Version 11.3(2)XA4, RELEASE SOFTWARE
(fc1)
Copyright (c) 1999 by cisco Systems, Inc.
TAC:Home:SW:IOS:Specials for info
C2600 platform with 32768 Kbytes of main memory
Enter the basic parameters
Continue with configuration dialog? [yes/no]:
yes
Would you like to enter basic management setup? [yes/no]: yes
Enter host name []: firebox
Enter enable secret [<Use current secret>]: eiger
Enter enable password []: moench
Enter virtual terminal password []: jungfrau
Configure SNMP Network Management? [no]: no
Enter interface name used to connect to the
management network from the above interface summary: FastEthernet0/0
Configuring interface FastEthernet0/0:
Use the 100 Base-TX (RJ-45) connector? [yes]: yes
Operate in full-duplex mode? [no]: no
Configure IP on this interface? [yes]: yes
IP address for this interface []: 192.168.102.200
Subnet mask for this interface [] : 255.255.255.0
Class C network is 192.168.102.0, 24 subnet bits; mask is /24
[0] Go to the IOS command prompt without saving this config.
[1] Return back to the setup without saving this config.
[2] Save this configuration to nvram and exit.
Enter your selection [2]: 2
CISCO TFTP-Server
- Load CD-ROM
- Click on Tftpserv.exe, install it in C:\TFTP
- Start TFTP
- Menü: View/Options: TFTP server root directory: C:\TFTP\root
firebox# sh flash
System flash directory:
File Length Name/status 1 4519168 C2600-IP_FW_MZ-120-7
[4519232 bytes used, 3869376 available, 8388608 total]
8192K bytes of processor board System flash (Read/Write)
firebox# copy flash tftp
Source filename []? C2600-IP_FW_MZ-120-7
Address or name of remote host []? 192.168.102.147
Destination filename []? C2600-IP_FW_MZ-120-7
The current IOS image is now saved to the Admin
Workstation.
- Insert CD-ROM
- Go to E:\Images\12.0
- Look at Info File using Notepad: RIL.idf for the correct
OS
- We used aaa1314.bin Cisco 2600 IOS IP/FW Feature
Set 12.0(7)XK1
- Copy aaa1314.bin to TFTP directory: C:\TFTP\root
Load Image to Router:
firebox> enable
firebox2# copy tftp flash
Address or name of remote host []? 192.168.102.147
Source filename []? aaa1314.bin
Destination filename [aaa1314.bin]?
Accessing tftp://192.168.102.147/aaa1314.bin...
Erase flash: before copying? [confirm]
Erasing the flash filesystem will remove all files! [confirm]
Erasing device...erased
Erase of flash: complete
Loading aaa1314.bin from 192.168.102.147 (via FastEthernet0/0):
[OK - 4519168/9037824 bytes]
Verifying checksum... OK (0x37C6)
4519168 bytes copied in 56.244 secs (80699 bytes/sec)
firebox2# reload
Proceed with reload? [confirm]
firebox> enable
firebox# copy running-config tftp
Address or name of remote host []? 192.168.102.147
Destination filename [firebox2-confg]?
738 bytes copied in 2.4 secs (369 bytes/sec)
firebox> enable
firebox# copy tftp running-config
Address or name of remote host []? 192.168.102.147
Source filename []? firebox2-confg
Destination filename [running-config]?
Accessing tftp://192.168.102.17/firebox2-confg...
Loading firebox2-confg from 192.168.102.17 (via FastEthernet0/0): !
[OK - 2653/5120 bytes]
2653 bytes copied in 1.244 secs (2653 bytes/sec)
!
version 12.0
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
service password-encryption
!
hostname firebox
!
logging buffered 4096 debugging
no logging console
enable secret 5 xxxxxxxxxxxxxxxxx
enable password 7 xxxxxxxxxxxxxxxxx
!
ip subnet-zero
no ip domain-lookup
!
ip inspect max-incomplete high 1100
ip inspect one-minute high 1100
ip inspect udp idle-time 60
ip inspect dns-timeout 10
ip inspect name CBAC1 tcp timeout 3600
ip inspect name CBAC1 udp timeout 15
ip inspect name CBAC1 ftp timeout 3600
ip inspect name CBAC1 rcmd timeout 3600
ip inspect name CBAC1 smtp timeout 3600
ip inspect name CBAC1 sqlnet timeout 3600
ip inspect name CBAC1 tftp timeout 30
ip inspect name CBAC2 tcp timeout 3600
ip inspect name CBAC2 ftp timeout 3600
ip inspect name CBAC2 udp timeout 15
ip inspect name CBAC2 rcmd timeout 3600
ip inspect name CBAC2 smtp timeout 3600
ip inspect name CBAC2 sqlnet timeout 3600
ip inspect name CBAC2 tftp timeout 30
ip audit notify log
ip audit po max-events 100
!
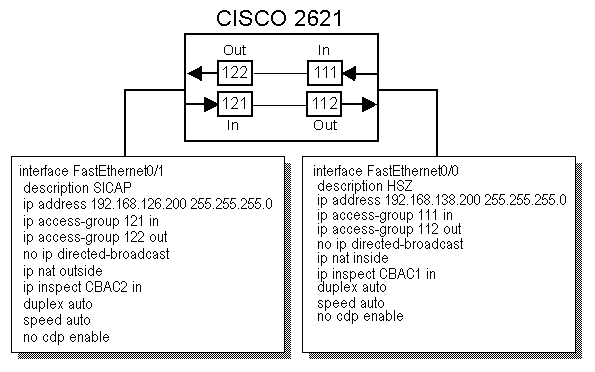
interface FastEthernet0/0
description HSZ
ip address 192.168.102.200 255.255.255.0
ip access-group 111 in
ip access-group 112 out
no ip directed-broadcast
ip nat inside
ip inspect CBAC1 in
duplex auto
speed auto
no cdp enable
!
interface FastEthernet0/1
description SICAP
ip address 192.168.101.200 255.255.255.0
ip access-group 121 in
ip access-group 122 out
no ip directed-broadcast
ip nat outside
ip inspect CBAC2 in
duplex auto
speed auto
no cdp enable
!
ip default-gateway 192.168.102.1
ip nat inside source list 1 interface FastEthernet0/1 overload
ip classless
ip route 140.20.110.142 255.255.255.0 192.168.101.100
ip route 194.75.121.206 255.255.255.255 192.168.101.100
ip route 194.75.121.207 255.255.255.255 192.168.101.100
no ip http server
!
access-list 1 permit 192.168.102.0 0.0.0.255
access-list 111 permit ip 192.168.102.0 0.0.0.255 any
access-list 111 deny ip any any
access-list 112 permit ip any any
access-list 121 permit icmp any any administratively-prohibited
access-list 121 permit icmp any any echo
access-list 121 permit icmp any any echo-reply
access-list 121 permit icmp any any packet-too-big
access-list 121 permit icmp any any time-exceeded
access-list 121 permit icmp any any unreachable
access-list 121 deny ip any any log
access-list 122 permit ip any any
no cdp run
banner motd Akadia AG
Information Technology
Arvenweg 4
CH-3604 Thun
!
line con 0
exec-timeout 0 0
password 7 xxxxxxxxxxxxxxxxx
login
transport input none
line aux 0
line vty 0 4
password 7 xxxxxxxxxxxxxxxxx
login
!
no scheduler allocate
end
|